实验环境:
操作系统:Mac OS X 10.11.4(当时最新正式版),模拟器:GNS3 IOU for Mac 1.4.5(当时最新版本)
注:当然,只要有思科模拟器都可以做这个实验
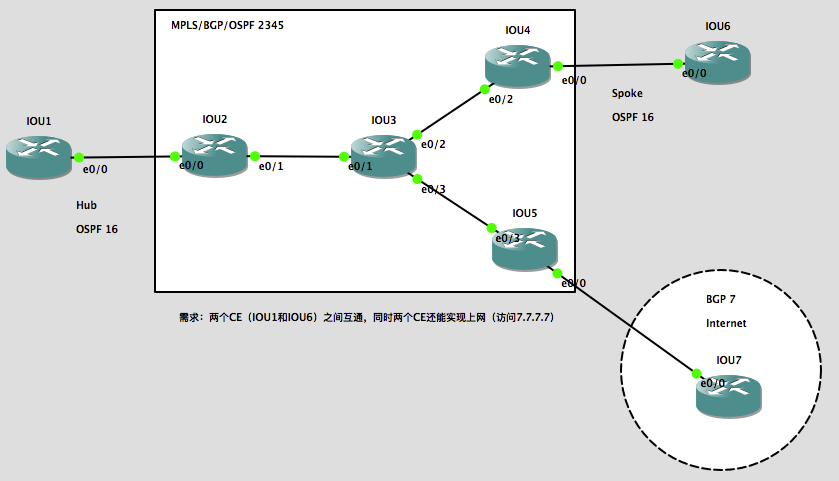
拓扑额外描述:
- IOU1和IOU6的rd值和rt import/export值都是2345:16;
- PE和CE之间使用的也是内网IP地址。
实验需求:
两个CE(IOU1和IOU6)之间互通,同时两个CE还能实现上网(访问全局路由表下的7.7.7.7)。
先根据图中的要求快速完成MPLS VPN的配置:
| IOU2:
conf t int e 0/0 int e 0/1 router os 2345 int r e 0/1 , l 0 ip cef int e 0/1 ip vrf IOU1 int e 0/0 router bgp 2345 add vpnv4 un add ipv4 un add ipv4 vrf IOU1 router os 16 vrf IOU1 |
IOU3:
conf t int e 0/1 int e 0/2 int e 0/3 router os 2345 int r e 0/1-3 , l 0 ip cef int r e 0/1-3 router bgp 2345 add vpnv4 un add ipv4 un |
IOU4:
conf t int e 0/0 int e 0/2 router os 2345 int r e 0/2 , l 0 ip cef int e 0/2 ip vrf IOU6 int e 0/0 router bgp 2345 add vpnv4 un add ipv4 un add ipv4 vrf IOU6 router os 16 vrf IOU6 |
| IOU1:
conf t int e 0/0 router os 16 |
IOU6:
conf t int e 0/0 router os 16 |
| IOU5:
conf t int e 0/3 int e 0/0 router os 2345 int r e 0/3 , l 0 ip cef int e 0/3 router bgp 2345 |
IOU7:
conf t int e 0/0 router bgp 7 |
实验过程:
1、在IOU2的vrf IOU1上写一条静态默认路由:
ip route vrf IOU1 0.0.0.0 0.0.0.0 5.5.5.5 global
2、在IOU2上为CE下发默认路由:
router ospf 16 vrf IOU1 default-information originate
3、在IOU2上通告loopback 0的IP地址到互联网:
router bgp 2345 add ipv4 un net 2.2.2.2 mask 255.255.255.255
4、在IOU2上做PAT(注意CE站点间的访问不用做PAT,要deny掉):
ip access-list extended VPN deny ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255 permit ip 192.168.0.0 0.0.255.255 any ip nat inside source list VPN interface loopback 0 vrf IOU1 overload int e 0/0 ip nat inside int e 0/1 ip nat outside
5、测试:
IOU1可以访问外网:
IOU1#p 7.7.7.7 so l 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 7.7.7.7, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms IOU1#tra 7.7.7.7 so l 0 Type escape sequence to abort. Tracing the route to 7.7.7.7 VRF info: (vrf in name/id, vrf out name/id) 1 172.16.12.2 6 msec 5 msec 5 msec 2 23.1.1.3 [MPLS: Label 18 Exp 0] 1 msec 1 msec 1 msec 3 35.1.1.5 0 msec 4 msec 6 msec 4 57.1.1.7 5 msec 5 msec 6 msec
在IOU6上deb ip icmp,看一下IOU1访问IOU6的源IP地址有没有经过PAT转换:
IOU6#deb ip icmp ICMP packet debugging is on IOU1#p 192.168.2.1 so l 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.2.1, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/5/12 ms
可以看到,从IOU1来的数据包没有经过PAT转换:
IOU6# *Mar 28 07:32:01.972: ICMP: echo reply sent, src 192.168.2.1, dst 192.168.1.1, topology BASE, dscp 0 topoid 0 *Mar 28 07:32:01.977: ICMP: echo reply sent, src 192.168.2.1, dst 192.168.1.1, topology BASE, dscp 0 topoid 0 *Mar 28 07:32:01.983: ICMP: echo reply sent, src 192.168.2.1, dst 192.168.1.1, topology BASE, dscp 0 topoid 0 *Mar 28 07:32:01.992: ICMP: echo reply sent, src 192.168.2.1, dst 192.168.1.1, topology BASE, dscp 0 topoid 0 *Mar 28 07:32:01.998: ICMP: echo reply sent, src 192.168.2.1, dst 192.168.1.1, topology BASE, dscp 0 topoid 0
现在我们在IOU6上做一下上述的配置,让IOU6也能上互联网:
1、在IOU4的vrf IOU6上写一条静态默认路由:
ip route vrf IOU6 0.0.0.0 0.0.0.0 5.5.5.5 global
2、在IOU4上为CE下发默认路由:
router ospf 16 vrf IOU6 default-information originate
3、在IOU4上通告loopback 0的IP地址到互联网:
router bgp 2345 add ipv4 un net 4.4.4.4 mask 255.255.255.255
4、在IOU4上做PAT(注意CE站点间的访问不用做PAT,要deny掉):
ip access-list extended VPN deny ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255 permit ip 192.168.0.0 0.0.255.255 any ip nat inside source list VPN interface loopback 0 vrf IOU6 overload int e 0/0 ip nat inside int e 0/2 ip nat outside
5、测试:
IOU6可以访问外网:
IOU6#p 7.7.7.7 so l 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 7.7.7.7, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/5/9 ms IOU6#tra 7.7.7.7 so l 0 Type escape sequence to abort. Tracing the route to 7.7.7.7 VRF info: (vrf in name/id, vrf out name/id) 1 172.16.46.4 6 msec 6 msec 4 msec 2 34.1.1.3 [MPLS: Label 18 Exp 0] 5 msec 6 msec 7 msec 3 35.1.1.5 5 msec 9 msec 8 msec 4 57.1.1.7 13 msec 6 msec 5 msec
在IOU1上deb ip icmp,看一下IOU6访问IOU1的源IP地址有没有经过PAT转换:
IOU1#deb ip icmp ICMP packet debugging is on IOU6#p 192.168.1.1 so l 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 2/6/11 ms
可以看到,从IOU6来的数据包没有经过PAT转换:
IOU1# *Mar 28 08:18:14.915: ICMP: echo reply sent, src 192.168.1.1, dst 192.168.2.1, topology BASE, dscp 0 topoid 0 *Mar 28 08:18:14.916: ICMP: echo reply sent, src 192.168.1.1, dst 192.168.2.1, topology BASE, dscp 0 topoid 0 *Mar 28 08:18:14.922: ICMP: echo reply sent, src 192.168.1.1, dst 192.168.2.1, topology BASE, dscp 0 topoid 0 *Mar 28 08:18:14.931: ICMP: echo reply sent, src 192.168.1.1, dst 192.168.2.1, topology BASE, dscp 0 topoid 0 *Mar 28 08:18:14.938: ICMP: echo reply sent, src 192.168.1.1, dst 192.168.2.1, topology BASE, dscp 0 topoid 0
其他相关文章:

发表评论?