IPSec Over GRE:是先 IPSec 后 GRE —— 即数据包中内层是 IPSec ,外层是 GRE ;
GRE Over IPSec:是先 GRE 后 IPSec —— 即数据包中内层是 GRE ,外层是 IPSec 。(本篇说明的是这个)
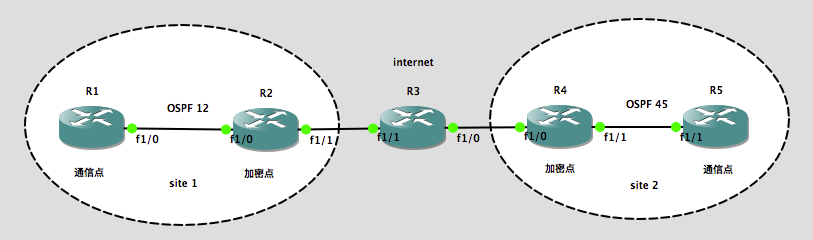
实验环境:
操作系统:Mac OS X 10.11.5 Beta 1(当时最新测试版),模拟器:GNS3 IOU for Mac 1.4.5(当时最新版本)
注:当然,只要有思科模拟器都可以做这个实验
实验需求:
site 1 和 site 2 均需要开启 OSPF ,实现 R1 到 R5 的内网通信,同时穿过 Internet 的流量需要加密。
实验步骤:(基础配置)
| R1 :
interface Loopback0 interface FastEthernet1/0 router ospf 12 |
R3 :
interface FastEthernet1/0 interface FastEthernet1/1 |
R5 :
interface Loopback0 interface FastEthernet1/1 router ospf 45 |
| R2 :
interface Loopback0 interface FastEthernet1/0 interface FastEthernet1/1 ip route 0.0.0.0 0.0.0.0 23.1.1.3 router ospf 12 |
R4 :
interface Loopback0 interface FastEthernet1/0 interface FastEthernet1/1 ip route 0.0.0.0 0.0.0.0 34.1.1.3 router ospf 45 |
GRE 的配置:
R2 :
R2(config)#int tunnel 0
R2(config-if)#tunnel source f 1/1
R2(config-if)#tunnel destination 34.1.1.4 —— tunnel mode 默认就是 gre ,可以不
配置 tunnel mode gre 这条命令
R2(config-if)#ip add 24.1.1.2 255.255.255.0
R2(config-if)#ip ospf 12 a 0
R4 :
R4(config)#int tunnel 0 R4(config-if)#tunnel source f 1/0 R4(config-if)#tunnel destination 23.1.1.2 R4(config-if)#ip add 24.1.1.4 255.255.255.0 R4(config-if)#ip ospf 45 a 0
IPSec 的配置:
R2 :
cry is en crypto isakmp policy 10 encr 3des hash md5 authentication pre-share crypto isakmp key cisco address 34.1.1.4 crypto ipsec transform-set trans esp-des esp-md5-hmac mode tunnel crypto map test 10 ipsec-isakmp set peer 34.1.1.4 set transform-set trans
R4 :
cry is en crypto isakmp policy 10 encr 3des hash md5 authentication pre-share crypto isakmp key cisco address 23.1.1.2 crypto ipsec transform-set trans esp-des esp-md5-hmac mode tunnel crypto map test 10 ipsec-isakmp set peer 23.1.1.2 set transform-set trans
捕获 GRE 的感兴趣流到 IPSec :
R2 :
R2(config)#ip access-list ex GRE
R2(config-ext-nacl)#per gre any any —— 捕捉 GRE 流然后放入 IPSec ,也就是先 GRE 后 IPSec
R2(config)#cry map test 10
R2(config-crypto-map)#match address GRE
R2(config)#int f 1/1
R2(config-if)#cry map test
R4 :
R4(config)#ip access-list ex GRE R4(config-ext-nacl)#per gre any any R4(config)#cry map test 10 R4(config-crypto-map)#match add GRE R4(config)#int f 1/0 R4(config-if)#cry map test
测试:
R1#p 5.5.5.5 so l 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 68/84/112 ms
本文完。如有疑问,欢迎在下方留言;如本文有什么错误,欢迎在下方留言指正,谢谢。
其他相关文章:

发表评论?