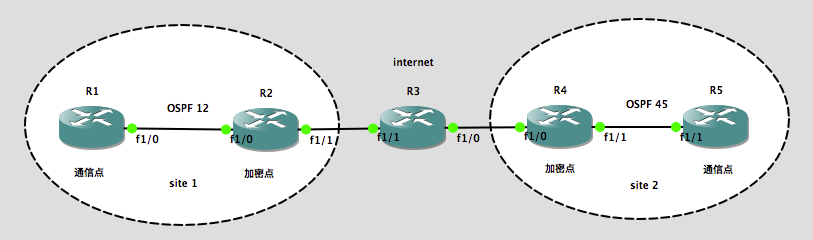
实验环境:
操作系统:Mac OS X 10.11.5 Beta 1(当时最新测试版),模拟器:GNS3 IOU for Mac 1.4.5(当时最新版本)
注:当然,只要有思科模拟器都可以做这个实验
实验需求:
site 1 和 site 2 均需要开启 OSPF ,实现 R1 到 R5 的内网通信,同时穿过 Internet 的流量需要加密。
实验步骤:(基础配置)
| R1 :
interface Loopback0 interface FastEthernet1/0 router ospf 12 |
R3 :
interface FastEthernet1/0 interface FastEthernet1/1 |
R5 :
interface Loopback0 interface FastEthernet1/1 router ospf 45 |
| R2 :
interface Loopback0 interface FastEthernet1/0 interface FastEthernet1/1 ip route 0.0.0.0 0.0.0.0 23.1.1.3 router ospf 12 |
R4 :
interface Loopback0 interface FastEthernet1/0 interface FastEthernet1/1 ip route 0.0.0.0 0.0.0.0 34.1.1.3 router ospf 45 |
IPSec 的配置:
R2 :
1 、开启 isakmp : R2(config)#crypto isakmp enable 2 、isakmp 策略: R2(config)#crypto isakmp policy 10 R2(config-isakmp)#encryption 3des R2(config-isakmp)#hash md5 R2(config-isakmp)#authentication pre-share R2(config-isakmp)#group 2 3 、认证密钥: R2(config)#crypto isakmp key Cisco address 34.1.1.4 4 、IPSec SA 策略: R2(config)#ip access-list extended VPN R2(config-ext-nacl)#per ip host 1.1.1.1 host 5.5.5.5 5 、转换集(把感兴趣流转换成加密的流量): R2(config)#crypto ipsec transform-set trans esp-des esp-md5-hmac R2(cfg-crypto-trans)#mode tunnel —— 详情请见《 IPSec 的两种工作模式及其报文封装格式》 6 、关联 R2(config)#crypto map test 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. R2(config-crypto-map)#match address VPN R2(config-crypto-map)#set transform-set trans R2(config-crypto-map)#set peer 34.1.1.4 7 、应用到接口 R2(config)#int f 1/1 R2(config-if)#crypto map test
R4 :
1 、开启 isakmp : R4(config)#crypto isakmp enable 2 、isakmp 策略: R4(config)#crypto isakmp policy 10 R4(config-isakmp)#encryption 3des R4(config-isakmp)#hash md5 R4(config-isakmp)#authentication pre-share R4(config-isakmp)#group 2 3 、认证密钥: R4(config)#crypto isakmp key cisco address 23.1.1.2 4 、IPSec SA 策略: R4(config)#ip access-list extended VPN R4(config-ext-nacl)#per ip host 5.5.5.5 host 1.1.1.1 5 、转换集(把感兴趣流转换成加密的流量): R4(config)#crypto ipsec transform-set trans esp-des esp-md5-hmac R4(cfg-crypto-trans)#mode tunnel 6 、关联 R4(config)#crypto map test 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. R4(config-crypto-map)#match address VPN R4(config-crypto-map)#set transform-set trans R4(config-crypto-map)#set peer 23.1.1.2 7 、应用到接口 R4(config)#int f 1/0 R4(config-if)#crypto map test
| R2 IPSec 配置汇总:
conf t cry is en crypto isakmp policy 10 crypto isakmp key cisco address 34.1.1.4 ip access-list extended VPN crypto ipsec transform-set trans esp-des esp-md5-hmac crypto map test 10 ipsec-isakmp int f 1/1 |
R4 IPSec 配置汇总:
conf t cry is en crypto isakmp policy 10 crypto isakmp key cisco address 23.1.1.2 ip access-list extended VPN crypto ipsec transform-set trans esp-des esp-md5-hmac crypto map test 10 ipsec-isakmp int f 1/0 |
测试:
R1#p 5.5.5.5 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 68/75/84 ms
8 、show
R2#sh crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 34.1.1.4 23.1.1.2 QM_IDLE 1001 ACTIVE IPv6 Crypto ISAKMP SA R2#sh crypto ipsec sa interface: FastEthernet1/1 Crypto map tag: test, local addr 23.1.1.2 protected vrf: (none) local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/0/0) —— IP 地址、掩码、协议号、端口号 remote ident (addr/mask/prot/port): (5.5.5.5/255.255.255.255/0/0) current_peer 34.1.1.4 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 —— 加解密的报文 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0 local crypto endpt.: 23.1.1.2, remote crypto endpt.: 34.1.1.4 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet1/1 current outbound spi: 0xB708F445(3070817349) PFS (Y/N): N, DH group: none inbound esp sas: spi: 0x29CA02B(43819051) transform: esp-des esp-md5-hmac , in use settings ={Tunnel, } conn id: 1, flow_id: SW:1, sibling_flags 80000040, crypto map: test sa timing: remaining key lifetime (k/sec): (4185375/3545) IV size: 8 bytes replay detection support: Y Status: ACTIVE(ACTIVE) inbound ah sas: inbound pcp sas: outbound esp sas: spi: 0xB708F445(3070817349) —— 安全关联索引 transform: esp-des esp-md5-hmac , in use settings ={Tunnel, } conn id: 2, flow_id: SW:2, sibling_flags 80000040, crypto map: test sa timing: remaining key lifetime (k/sec): (4185375/3545) IV size: 8 bytes replay detection support: Y Status: ACTIVE(ACTIVE) outbound ah sas: outbound pcp sas: R2#show crypto engine connections active Crypto Engine Connections ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address 1 IPsec DES+MD5 0 4 4 23.1.1.2 2 IPsec DES+MD5 4 0 0 23.1.1.2 1001 IKE MD5+3DES 0 0 0 23.1.1.2 R2#sh crypto session Crypto session current status Interface: FastEthernet1/1 Session status: UP-ACTIVE Peer: 34.1.1.4 port 500 IKEv1 SA: local 23.1.1.2/500 remote 34.1.1.4/500 Active IPSEC FLOW: permit ip host 1.1.1.1 host 5.5.5.5 Active SAs: 2, origin: crypto map
关于 IPSec 的一些 ACL 应用:
接下来通过几个例子来说明一下。
IPSec peer 入方向 ACL 的处理过程:
( 1 )在 R2 的 f 1/1 口挂载一个入方向的 access-list ,仅放行 ESP 协议的数据包:
R2(config)#access-list 100 per esp any any R2(config-if)#int f 1/1 R2(config-if)#ip access-group 100 in
R1#p 5.5.5.5 so 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 68/72/88 ms
R2#sh ip acce 100
Extended IP access list 100
10 permit esp any any (5 matches) —— 匹配了 5 个报文
sa 被干掉后需要重新协商,但是我们只放行了 ESP ,没有放行其他协议的数据包,所以无法重新协商,也就 ping 不通了:
R2#clear crypto sa R1#p 5.5.5.5 so 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 ..... Success rate is 0 percent (0/5)
放行 isakmp 协议的数据包后就可以协商成功并建立通信了:
R2(config)#access-list 100 permit udp any eq isakmp any eq isakmp R1#p 5.5.5.5 so 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 56/66/72 ms
( 2 )在 R2 的 cry map 上挂载一个入方向的 access-list ,放行源 IP 地址为 5.5.5.5 且目的 IP 地址为 1.1.1.1 的 telnet 协议数据包,再拒绝放行任何 ICMP 协议的数据包:
R2(config)#access-list 101 per tcp h 5.5.5.5 h 1.1.1.1 eq telnet
R2(config)#access-list 101 deny icmp any any
R2(config)#crypto map test 10
R2(config-crypto-map)#set ip access-group 101 in
R2(config)#int f 1/1
R2(config-if)#no cry map test —— 需要重新应用一下,不然不生效!!!
R2(config-if)#cry map test
这里想说明的是 cry map 里的 access-list 是在流量被解密后才去匹配的(因为 R2 的 f 1/1 口的入方向上已经挂载了一个仅放行 ESP 协议数据包的 access-list ,所以如果 telnet 协议数据包能从 R2 的 f 1/1 口进来,且 R5 ping 不通 R1 ,说明 cry map 里的 access-list 是在流量被解密后才去匹配的):
R1(config)#line vty 0 4 R1(config-line)#pass cisco R5#p 1.1.1.1 so 5.5.5.5 —— 不通,因为流量被解密以后,会重新撞上 cry map 里设置的 ACL Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds: Packet sent with a source address of 5.5.5.5 ..... Success rate is 0 percent (0/5) R5#telnet 1.1.1.1 /source-interface l 0 Trying 1.1.1.1 ... Open User Access Verification Password: R1>ex [Connection to 1.1.1.1 closed by foreign host] R2#sh ip acce Extended IP access list 100 10 permit esp any any (46 matches) 20 permit udp any eq isakmp any eq isakmp (7 matches) Extended IP access list 101 10 permit tcp host 5.5.5.5 host 1.1.1.1 eq telnet (24 matches) —— 匹配上了 20 deny icmp any any (4 matches)—— 匹配上了 Extended IP access list VPN 10 permit ip host 1.1.1.1 host 5.5.5.5 (61 matches)
IPSec peer 出方向 ACL 的处理过程:
( 1 )接上,此时 R1 是 ping 不通 R5 的:
R1#p 5.5.5.5 so 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 ..... Success rate is 0 percent (0/5)
修改 R2 的 cry map 上的 access-list 101 ,放行源 IP 地址为 5.5.5.5 且目的 IP 地址为 1.1.1.1 的 ICMP 协议的 echo-reply 数据包:
R2(config)#ip acce ex 101 R2(config-ext-nacl)#15 per icmp h 5.5.5.5 h 1.1.1.1 echo-reply
现在 R1 可以 ping 通 R5 了(但是 R5 还 ping 不通 R1 ):
R1#p 5.5.5.5 so 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 68/84/144 ms R5#p 1.1.1.1 so 5.5.5.5 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds: Packet sent with a source address of 5.5.5.5 ..... Success rate is 0 percent (0/5)
再在 R2 的 cry map 上挂载一个出方向的 access-list ,放行源 IP 地址为 1.1.1.1 且目的 IP 地址为 5.5.5.5 的 telnet 协议数据包,再拒绝放行源 IP 地址为 1.1.1.1 且目的 IP 地址为 5.5.5.5 的 ICMP 协议的 echo 数据包(再修改 access-list 101 放行反方向回来的 telnet 协议数据包):
R2(config)#acce 102 per tcp h 1.1.1.1 h 5.5.5.5 eq telnet
R2(config)#acce 102 deny icmp h 1.1.1.1 h 5.5.5.5 echo
R2(config)#cry map test 10
R2(config-crypto-map)#set ip access-group 102 out
R2(config)#int f 1/1
R2(config-if)#no cry map test
R2(config-if)#cry map test
R2(config)#access-list 101 per tcp h 5.5.5.5 eq telnet h 1.1.1.1 —— 流量双向放行才能通
R5(config)#line vty 0 4
R5(config-line)#pass cisco
现在可以看到 R1 ping 不通 R5 了,但是 R1 可以 telnet R5 ,与入方向 ACL 处理过程中的第( 2 )个例子类似:
R1#p 5.5.5.5 so 1.1.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds: Packet sent with a source address of 1.1.1.1 ..... Success rate is 0 percent (0/5) R1#telnet 5.5.5.5 /source-interface l 0 Trying 5.5.5.5 ... Open User Access Verification Password: Password: R5> R5> R5>ex [Connection to 5.5.5.5 closed by foreign host]
( 2 )在 R2 的 f 1/1 口挂载一个出方向的 access-list ,仅放行 ESP 协议的数据包:
R2(config)#acc 103 per esp any any R2(config)#int f 1/1 R2(config-if)#ip access-group 103 out
R1#telnet 5.5.5.5 /source-interface l 0
Trying 5.5.5.5 ... Open
User Access Verification
Password:
R5>ex
[Connection to 5.5.5.5 closed by foreign host]
R2#sh ip acce
Extended IP access list 100
10 permit esp any any (116 matches)
20 permit udp any eq isakmp any eq isakmp (12 matches)
Extended IP access list 101
10 permit tcp host 5.5.5.5 host 1.1.1.1 eq telnet (26 matches)
15 permit icmp host 5.5.5.5 host 1.1.1.1 echo-reply (15 matches)
20 deny icmp any any (14 matches)
30 permit tcp host 5.5.5.5 eq telnet host 1.1.1.1 (43 matches)
Extended IP access list 102
10 permit tcp host 1.1.1.1 host 5.5.5.5 eq telnet (56 matches)
20 deny icmp host 1.1.1.1 host 5.5.5.5 echo (8 matches)
Extended IP access list 103
10 permit esp any any (22 matches) —— 匹配上了
Extended IP access list VPN
10 permit ip host 1.1.1.1 host 5.5.5.5 (150 matches)
clear 掉:
R2#clear cry sa R2#clear cry is R4#clear cry sa R4#clear cry is
R1 去 telnet R5 竟然通了,与入方向 ACL 处理过程中的第( 1 )个例子的结果不一致,因为 IPsec 流量是从 R2 开始产生的,自己产生的流量是不能 deny 的:
R1#telnet 5.5.5.5 /source-interface l 0 Trying 5.5.5.5 ... Open User Access Verification Password: R5>ex [Connection to 5.5.5.5 closed by foreign host]

发表评论?