| 如需注册 @ccie.engineer、@ccde.engineer、@ccar.engineer、@hcie.engineer、@rhce.engineer 和 @cissp.engineer 邮箱,请点击这里。 |
实验环境:
操作系统:Mac OS X 10.11.4(当时最新正式版),模拟器:GNS3 IOU for Mac 1.4.5(当时最新版本)
注:当然,只要有思科模拟器都可以做这个实验
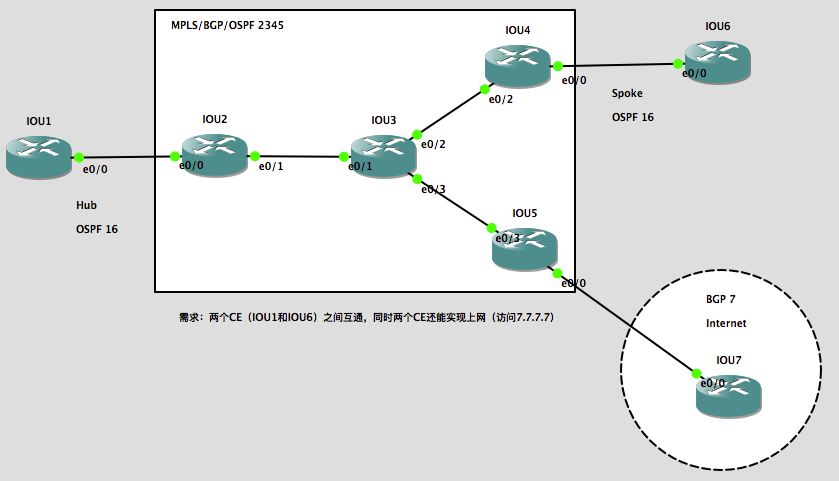
拓扑额外描述:
- IOU1和IOU6的rd值和rt import/export值都是2345:16;
- PE和CE之间使用的是公网IP地址,而CE内部(环回口)才是内网IP地址。
实验需求:
两个CE(IOU1和IOU6)之间互通,同时两个CE还能实现上网(访问全局路由表下的7.7.7.7)。
先根据图中的要求快速完成MPLS VPN的配置:
| IOU2:
conf t int e 0/0 int e 0/1 router os 2345 int r e 0/1 , l 0 ip cef int e 0/1 ip vrf IOU1 int e 0/0 router bgp 2345 add vpnv4 un add ipv4 un add ipv4 vrf IOU1 router os 16 vrf IOU1 |
IOU3:
conf t int e 0/1 int e 0/2 int e 0/3 router os 2345 int r e 0/1-3 , l 0 ip cef int r e 0/1-3 router bgp 2345 add vpnv4 un add ipv4 un |
IOU4:
conf t int e 0/0 int e 0/2 router os 2345 int r e 0/2 , l 0 ip cef int e 0/2 ip vrf IOU6 int e 0/0 router bgp 2345 add vpnv4 un add ipv4 un add ipv4 vrf IOU6 router os 16 vrf IOU6 |
| IOU5:
conf t int e 0/3 int e 0/0 router os 2345 int r e 0/3 , l 0 ip cef int e 0/3 router bgp 2345 |
IOU7:
conf t int e 0/0 router bgp 7 |
| IOU1:
conf t int e 0/0 router os 16 |
IOU6:
conf t int e 0/0 router os 16 |
实验过程:
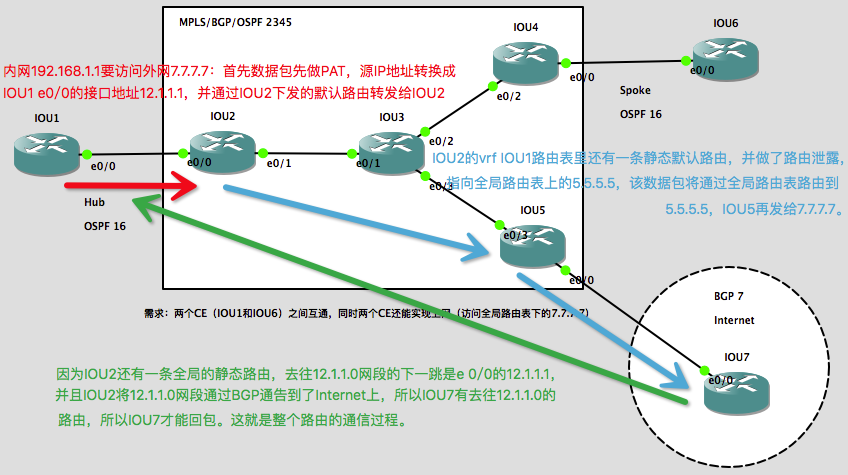
我们先来看看数据包是如何从CE传递到全局路由表上的:
1、在IOU2上写一条静态默认路由,做route leak,指向Internet:
ip route vrf IOU1 0.0.0.0 0.0.0.0 5.5.5.5 global
2、在IOU2上再写一条回包路由,并通过BGP通告:
ip route 12.1.1.0 255.255.255.0 e 0/0 12.1.1.1 router bgp 2345 add ipv4 un net 12.1.1.0 mask 255.255.255.0
3、在IOU2上往CE下发默认路由:
router os 16 vrf IOU1 default-information originate
4、IOU1上做NAT(注意:这里要做过滤,CE站点间的流量不做PAT):
ip access-list extended VPN deny ip any 192.168.0.0 0.0.255.255 permit ip 192.168.0.0 0.0.255.255 any ip nat inside source list VPN interface e 0/0 overload int e 0/0 ip nat outside int l 0 ip nat inside
现在VRF里的CE可以访问Internet了,成功ping通7.7.7.7:
IOU1#p 7.7.7.7 so l 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 7.7.7.7, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/5 ms IOU1#tra 7.7.7.7 so l 0 Type escape sequence to abort. Tracing the route to 7.7.7.7 VRF info: (vrf in name/id, vrf out name/id) 1 12.1.1.2 11 msec 4 msec 4 msec 2 23.1.1.3 [MPLS: Label 17 Exp 0] 5 msec 5 msec 5 msec 3 35.1.1.5 6 msec 2 msec 2 msec 4 57.1.1.7 5 msec 7 msec 1 msec
IOU1#sh ip nat translations Pro Inside global Inside local Outside local Outside global icmp 12.1.1.1:2 192.168.1.1:2 7.7.7.7:2 7.7.7.7:2 udp 12.1.1.1:49167 192.168.1.1:49167 7.7.7.7:33434 7.7.7.7:33434 udp 12.1.1.1:49168 192.168.1.1:49168 7.7.7.7:33435 7.7.7.7:33435 udp 12.1.1.1:49169 192.168.1.1:49169 7.7.7.7:33436 7.7.7.7:33436 udp 12.1.1.1:49170 192.168.1.1:49170 7.7.7.7:33437 7.7.7.7:33437 udp 12.1.1.1:49171 192.168.1.1:49171 7.7.7.7:33438 7.7.7.7:33438 udp 12.1.1.1:49172 192.168.1.1:49172 7.7.7.7:33439 7.7.7.7:33439 udp 12.1.1.1:49173 192.168.1.1:49173 7.7.7.7:33440 7.7.7.7:33440 udp 12.1.1.1:49174 192.168.1.1:49174 7.7.7.7:33441 7.7.7.7:33441 udp 12.1.1.1:49175 192.168.1.1:49175 7.7.7.7:33442 7.7.7.7:33442 udp 12.1.1.1:49176 192.168.1.1:49176 7.7.7.7:33443 7.7.7.7:33443 udp 12.1.1.1:49177 192.168.1.1:49177 7.7.7.7:33444 7.7.7.7:33444 udp 12.1.1.1:49178 192.168.1.1:49178 7.7.7.7:33445 7.7.7.7:33445
同时IOU1也能访问IOU6:
IOU1#tra 192.168.2.1 Type escape sequence to abort. Tracing the route to 192.168.2.1 VRF info: (vrf in name/id, vrf out name/id) 1 12.1.1.2 7 msec 6 msec 2 msec 2 23.1.1.3 [MPLS: Labels 17/22 Exp 0] 2 msec 1 msec 1 msec 3 46.1.1.4 [MPLS: Label 22 Exp 0] 5 msec 5 msec 5 msec 4 46.1.1.6 5 msec 5 msec 5 msec
实验按理来说到这里就结束了,但如果你还想在IOU6上做路由泄露,同时IOU1和IOU6之间能互相访问,你可以接着往下看。
1、在IOU4上写一条静态默认路由,做route leak,指向Internet:
ip route vrf IOU6 0.0.0.0 0.0.0.0 5.5.5.5 global
2、在IOU4上再写一条回包路由,并通过BGP通告:
ip route 46.1.1.0 255.255.255.0 e 0/0 46.1.1.6 router bgp 2345 add ipv4 un net 46.1.1.0 mask 255.255.255.0
3、在IO4上往CE下发默认路由:
router os 16 vrf IOU6 default-information originate
4、IOU6上做NAT(注意:这里要做过滤,CE站点间的流量不做PAT):
ip access-list extended VPN deny ip any 192.168.0.0 0.0.255.255 permit ip 192.168.0.0 0.0.255.255 any ip nat inside source list VPN interface e 0/0 overload int e 0/0 ip nat outside int l 0 ip nat inside
测试:
IOU6#p 7.7.7.7 so l 0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 7.7.7.7, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/4/9 ms IOU6#tra 7.7.7.7 so l 0 Type escape sequence to abort. Tracing the route to 7.7.7.7 VRF info: (vrf in name/id, vrf out name/id) 1 46.1.1.4 5 msec 5 msec 5 msec 2 34.1.1.3 [MPLS: Label 17 Exp 0] 1 msec 1 msec 0 msec 3 35.1.1.5 1 msec 1 msec 6 msec 4 57.1.1.7 2 msec 7 msec 8 msec
IOU6#sh ip nat translations Pro Inside global Inside local Outside local Outside global icmp 46.1.1.6:0 192.168.2.1:0 7.7.7.7:0 7.7.7.7:0 udp 46.1.1.6:49154 192.168.2.1:49154 7.7.7.7:33434 7.7.7.7:33434 udp 46.1.1.6:49155 192.168.2.1:49155 7.7.7.7:33435 7.7.7.7:33435 udp 46.1.1.6:49156 192.168.2.1:49156 7.7.7.7:33436 7.7.7.7:33436 udp 46.1.1.6:49157 192.168.2.1:49157 7.7.7.7:33437 7.7.7.7:33437 udp 46.1.1.6:49158 192.168.2.1:49158 7.7.7.7:33438 7.7.7.7:33438 udp 46.1.1.6:49159 192.168.2.1:49159 7.7.7.7:33439 7.7.7.7:33439 udp 46.1.1.6:49160 192.168.2.1:49160 7.7.7.7:33440 7.7.7.7:33440 udp 46.1.1.6:49161 192.168.2.1:49161 7.7.7.7:33441 7.7.7.7:33441 udp 46.1.1.6:49162 192.168.2.1:49162 7.7.7.7:33442 7.7.7.7:33442 udp 46.1.1.6:49163 192.168.2.1:49163 7.7.7.7:33443 7.7.7.7:33443 udp 46.1.1.6:49164 192.168.2.1:49164 7.7.7.7:33444 7.7.7.7:33444 udp 46.1.1.6:49165 192.168.2.1:49165 7.7.7.7:33445 7.7.7.7:33445
同时IOU1也能访问IOU6:
IOU6#tra 192.168.1.1 Type escape sequence to abort. Tracing the route to 192.168.1.1 VRF info: (vrf in name/id, vrf out name/id) 1 46.1.1.4 6 msec 8 msec 5 msec 2 34.1.1.3 [MPLS: Labels 16/23 Exp 0] 2 msec 1 msec 0 msec 3 12.1.1.2 [MPLS: Label 23 Exp 0] 1 msec 1 msec 0 msec 4 12.1.1.1 1 msec 1 msec 0 msec
这是思科官方的英文参考文档 — Route Leaking in MPLS/VPN Networks:
其他相关文章:
- 【实验】MPLS L3VPN中实现CE访问外网(Spoke CE从Hub CE访问外网)
- 【实验】MPLS L3VPN中实现CE访问外网(PE上PAT,VRF路由泄露到全局,NAT Awared VRF)
本文完。如有疑问,欢迎在下方留言;如本文有什么错误,欢迎在下方留言指正,谢谢。

发表评论?